Creating #CyberAware Habits
October 3-7
Figuring out how to keep your accounts and devices protected online can be a tedious, even confusing process, however if you have good #CyberAware habits, it doesn’t have to be so difficult. Things like creating strong passwords and setting up multi-factor authentication as soon as you set up a new online account are a few of the best ways to protect yourself online. You will still need to stay alert about your presence online, but simply having these habits will make things much easier. Take a look at some of the topics below to find out how you can create #CyberAware habits:
Creating Hacker-Resistant Passwords
Passphrases (SANS Institute)
Password Managers: How They Work and How to Choose (SANS Institute)
Two-Step Verification (SANS Institute)
*Most popular websites allow you to turn on multi- or two-factor authentication. Below are tutorials for some of the most popular sites. Check with your banking and credit card companies’ websites to see if they offer multi-factor authentication methods so you can secure your financial information, as well.
- GOOGLE: Enabling 2-Step Verification
- FACEBOOK: Enabling Login Approvals
- TWITTER: Enable Login Verification
- SNAPCHAT: How to Turn On 2FA
- LINKED IN: Turning Two-Step Verification On and Off
- AMAZON: Turning on Two-Step Verification
- YAHOO: Two-Step Verification
- APPLE: Two-Factor Authentication for Apple ID
Operating Systems:
Microsoft and Apple provide free security updates for their software products.
- Windows: Microsoft issues patches for all Microsoft products on the second Tuesday of each month, as well as out-of-cycle patches on any day of the month. This is a good occasion to check manually, a practice that you should follow once every two weeks, to make sure all of the updates have been installed. Find out how to check for Windows Updates here.
- Apple OS X: Updates are issued frequently. Click here for information on how to update Mac OS.
Software:
Program developers often find bugs, security vulnerabilities, or ways they can enhance their programs, and they frequently release “patches” or fixes to their users. For this reason, it is recommended to install software updates as they become available. Below are some of the more frequently used programs that need periodically patched:
- Browsers
Older, outdated, or non-patched versions of internet browsers contain multiple vulnerabilities that can lead to memory corruption, spoofing and execution of malicious scripts or code. It is absolutely critical to update your internet browsers. Get the latest versions of the most popular web browsers below:
- Adobe Flash Player
Click here to check your version of Adobe Flash Player.
- Adobe Acrobat Reader and Acrobat Pro
Follow the steps below in order to update Acrobat Reader and/or Acrobat Pro:
1. Launch Acrobat Reader or Acrobat Pro
2. Go to the ‘Help’ menu and select ‘Check for Updates’
3. Follow the recommendations provided by the ‘Adobe Updater Utility.’
- Java
Visit this link to check your Java version: http://java.com/en/download/help/testvm.xml
Securing Your New Tablet (SANS Institute)
Securely Using Mobile Apps (SANS Institute)
Protecting Yourself & Your Data
October 10-14
Now that you know the basics cyber security, how can you continue to protect yourself and your data? Data backups can be helpful in the event of a lost or damaged computer, and disk encryption will keep your data protected if your computer or storage media is stolen. To keep your reputation protected, use appropriate social media etiquette and know how to use public WiFi. Check out the links below to find out what you can do:
Encryption (SANS Institute)
Your operating system likely comes with its own encryption application. BitLocker was released with Windows Vista and is built-in to Windows Vista, Windows 7, Windows 8.1, and Windows 10. Apple’s FileVault 2 has been built-in to Mac OS X since version 10.7.
The safest way to use public WiFi is not to use it at all, however, that is not always practical. There are times when you might need to connect to a public network for work, school, or personal reason while avoiding excessive data charges. Take a look at the links below to find out how you can use public WiFi safely and securely.
Using Marshall University’s VPN
Staying Secure on the Road (SANS Institute)
Tips for Using Public WiFi Networks (Federal Trade Commission)
Privacy Tips for Using Public Computers & Wireless Networks (StopThinkConnect)
Recognizing Cybercrime
October 17-21
No matter how secure our online habits are, cybercrime still exists. Knowing how to spot a malicious website, program, or email can prevent your device from being infected or your personal information from being stolen. Learn how to be cautious using the links below:
Think you can spot a phishing email? Take this quiz to find out your Phishing IQ.
Phishing (SANS Institute)
CEO Fraud (SANS Institute) – Spear Phishing and Senior Executive Impersonation
What Is Malware? (SANS Institute)
Yes, You Actually Are a Target (SANS Institute)
Malware & Botnets (StaySafeOnline)
Ransomware (SANS Institute)
Ransomware Facts & Tips (StopThinkConnect)
If a website or web form asks for sensitive information, credit card/financial information, or prompts for a username and password, be sure to look for the “s” in “https://” at the beginning of the URL. If the web address has “http://” instead of “https://”, do not fill out the form or credentials on that page, as this means your data will not be encrypted when you submit. Instead it will be sent in plain text that a hacker can easily read.
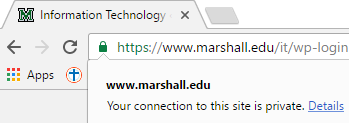
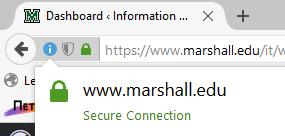
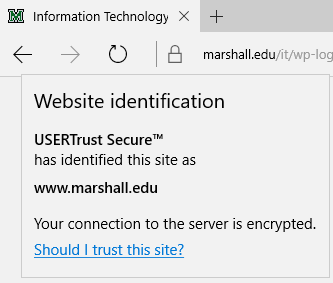
When you visit a secure, encrypted webpage, your browser will likely show a padlock or security icon to the left of the web address field. Check out the examples below to see what this looks like on the most popular browsers:
Google Chrome:
Firefox:
Microsoft Edge: (even though the browser is hiding the “https://” section of the web address, you can still click on the padlock to ensure its security)
Other Resources:
Online Shopping (StaySafeOnline)
How Can I Tell If a Web Page Is Secure? (SSL)
Understanding Web Site Certificates (US-CERT)
Reacting When Hacked
October 24-28
Despite our efforts to protect ourselves, sometimes the bad guys are still successful. But there are steps you can take to regain your sense of security and protect your information after being hacked. Visit the links below to learn what to do if you become a victim of cybercrime:
“I’m Hacked, Now What?” (SANS Institute)
Hacked Accounts (StaySafeOnline)
Download Free Antivirus – Symantec Endpoint Protection
Keep A Clean Machine (StopThinkConnect)
Get Rid of Malware (FTC)
Norton Power Eraser Tool (Norton)
So often we see in the news yet another report of a massive data breach, such as the one at Yahoo! in September. There are a couple of services you can subscribe to that will notify you if your email address has appeared in a massive data breach.
HaveIBeenPwned is a free resource for anyone to quickly assess if they are at risk due to an account compromise in a data breach. You can either search your email address(es) a single time to find out if it’s been breached in the past, or subscribe to the service so you will receive an alert if your account appears in a breach in the future.
Pastebin is a free resource used to share information online. It is mainly used by program developers to share pieces of source code, however hackers often use this page to share stolen credentials. Using the site in this manner is against Pastebin’s Acceptable Use Policy and they will remove these pastes as they are reported. If you create an account, you can subscribe to “MyAlerts” for free and enter up to 3 different email addresses. Pastebin will alert you if any of these email addresses show up in their pastes.
What to Do When You Receive a Data Breach Notice (Privacy Rights Clearing House)
What to Do After a Data Breach (Tom’s Guide)
National Cyber Security Alliance Statement Following Reported Massive Data Breach at Yahoo! Inc [Includes Advice] (StaySafeOnline)